Bypassing internet Positif: Understanding and Navigating DNS Filtering
Internet censorship is a growing concern worldwide, and Indonesia’s “Internet Positif” program is a prime example of such efforts. This program utilizes DNS filtering to block access to websites deemed inappropriate or harmful by the government. While intended to protect users, it can also restrict access to legitimate and valuable resources. This article delves into the mechanisms of DNS filtering, specifically within the context of Internet Positif, and explores methods to bypass these restrictions.
The Domain Name System (DNS) acts as the internet’s phonebook, translating human-readable domain names (like “example.com”) into numerical IP addresses (like “192.0.0.1”) that computers use to communicate. When you type a website address into your browser, your device sends a DNS query to a DNS server, which then returns the corresponding IP address.

Internet Positif leverages this process by manipulating DNS responses. When a user attempts to access a blocked website, the DNS server returns an incorrect IP address or no address at all, preventing the browser from establishing a connection. This is often accompanied by a redirect to a warning page indicating the site is blocked.
The Indonesian Ministry of Communication and Information Technology (Kominfo) maintains a blacklist of websites considered to violate Indonesian law or social norms. This blacklist includes sites related to pornography, gambling, radicalism, and other content deemed objectionable.
Here’s a breakdown of how the filtering typically works:
1. Blacklist Maintenance:

Kominfo constantly updates its blacklist, adding and removing websites based on reports and monitoring.
2. DNS Interception:
Internet Service Providers (ISPs) in Indonesia are required to implement Kominfo’s filtering. This is often achieved by configuring their DNS servers to intercept requests for blacklisted domains.
3. DNS Spoofing/Redirection:
When a user attempts to access a blocked domain, the ISP’s DNS server returns a fake IP address, often pointing to a block page or a non-existent server.
4. Block Page Display:
The user’s browser is redirected to a block page, informing them that the website is inaccessible due to Internet Positif filtering.
While the program’s intentions may be well-meaning, it often results in the blocking of legitimate websites, impacting freedom of information and access to resources. Common reasons for bypassing Internet Positif include:
1. Accessing Blocked Information:
Users may need to access blocked websites for research, educational purposes, or to access news sources that are critical of the government.
2. Freedom of Expression:
Many users believe that the government’s censorship is an infringement on their right to freedom of expression and access to information.
3. Circumventing Overly Broad Blocking:
The blacklist can sometimes be overly broad, blocking websites that are not actually harmful.
4. Protecting Privacy:
Some users may be concerned about the government’s monitoring of their online activity and seek to bypass the filtering to protect their privacy.
Several methods can be used to bypass Internet Positif filtering. Each method has its own advantages and disadvantages in terms of ease of use, speed, and security.
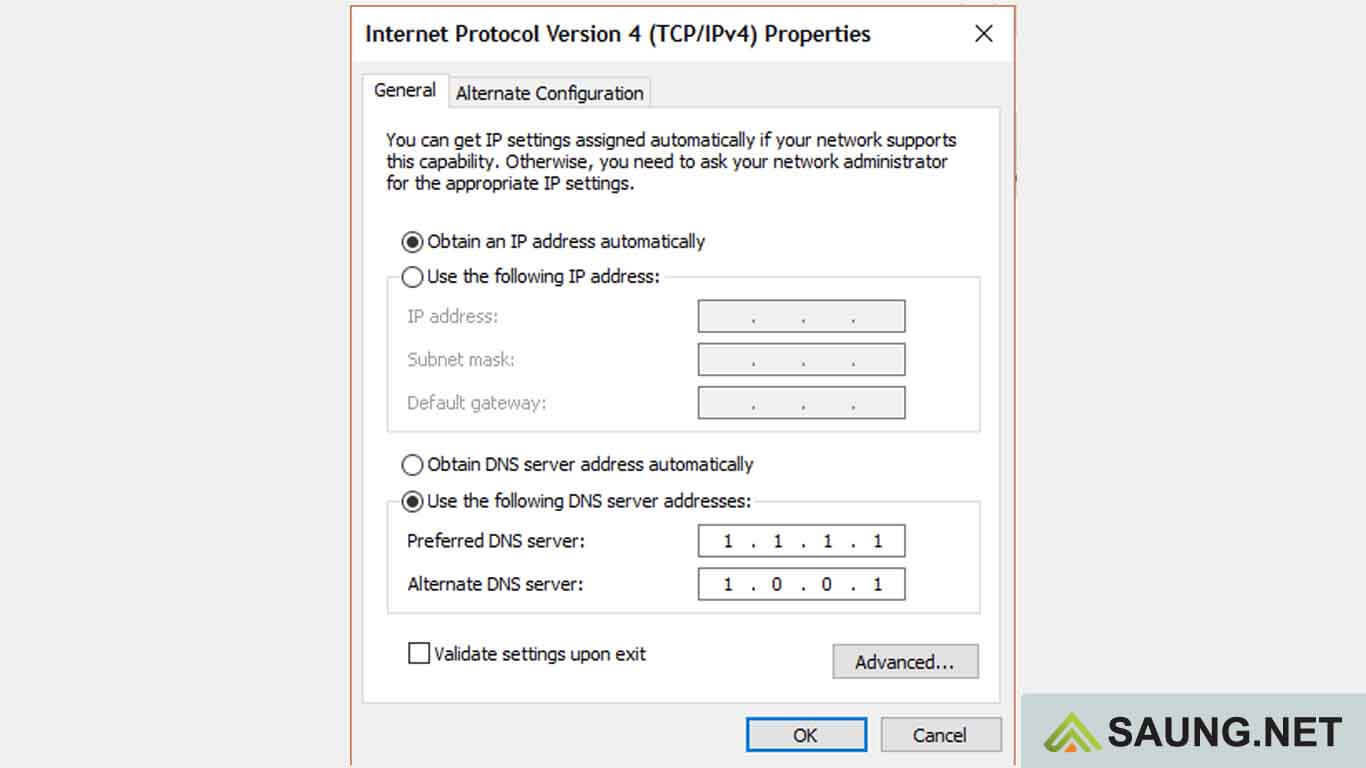
1. Changing DNS Servers:
This is the most common and straightforward method. By changing your device’s DNS settings to use a public DNS server, such as Google Public DNS (8.8.8.8 and 8.8.4.4) or Cloudflare DNS (1.1.1.1 and 1.0.0.1), you can bypass your ISP’s filtering. These public DNS servers do not typically implement Internet Positif filtering.
2. Using a Virtual Private Network (VPN):
A VPN creates an encrypted tunnel between your device and a remote server, masking your IP address and routing your traffic through the VPN server. This effectively bypasses DNS filtering and hides your online activity from your ISP.
3. Using a Proxy Server:
A proxy server acts as an intermediary between your device and the internet. Like a VPN, it can mask your IP address and bypass filtering. However, proxy servers are generally less secure than VPNs and may not encrypt your traffic.
4. Using Tor Browser:
The Tor Browser routes your traffic through a network of volunteer-operated servers, anonymizing your online activity and bypassing censorship. It is a powerful tool for privacy and security but can be slower than other methods.
5. Using DNS over HTTPS (DoH) or DNS over TLS (DoT):
DoH and DoT encrypt DNS queries, preventing ISPs from intercepting and manipulating them. By using DoH or DoT with a DNS server that supports these protocols, you can bypass DNS filtering.
6. Using Smart DNS:
Smart DNS services redirect only the traffic related to blocked websites, allowing you to maintain faster speeds for other online activities. Unlike VPNs, Smart DNS doesn’t encrypt your traffic.
While these methods can be effective in bypassing Internet Positif, it’s important to be aware of the potential risks and considerations:
1. Legal Implications:
While bypassing Internet Positif is generally not illegal for individual users, it’s important to be aware of the potential legal implications, especially if you are accessing content that is illegal under Indonesian law.
2. Security Risks:
Using untrusted VPNs or proxy servers can expose your device to malware and other security threats. It’s crucial to choose reputable providers.
3. Performance Impact:
Some methods, such as using Tor or free VPNs, can significantly impact your internet speed.
4. ISP Detection:
ISPs may be able to detect and block some methods of bypassing Internet Positif, such as VPNs or specific DNS servers.
5. Privacy Concerns:
Even when using methods to bypass filtering, your online activity may still be monitored by other entities, such as website operators or advertisers.
The best method for bypassing Internet Positif depends on your individual needs and priorities. If you prioritize ease of use and speed, changing DNS servers or using a reputable VPN is a good option. If you prioritize privacy and anonymity, Tor Browser may be more suitable.
Internet Positif, while intended to protect users, can restrict access to valuable resources and infringe on freedom of information. Understanding the mechanisms of DNS filtering and the available methods to bypass it empowers users to make informed choices about their online access. It is crucial to use these methods responsibly and be aware of the potential risks and legal implications. As technology evolves, so do the methods used to censor and bypass censorship, creating an ongoing dynamic between internet freedom and control.


